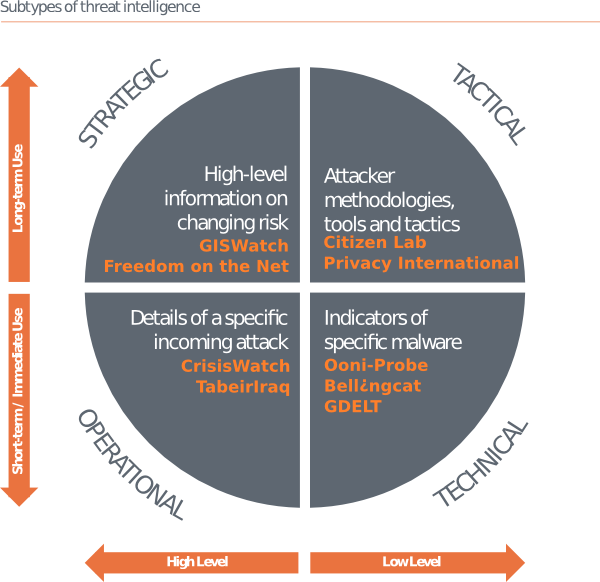
Tactical Human Rights Documentation
A Case for Human Rights Threat Intelligence
There is a growing exchange of legal language, political techniques, and censorship and surveillance technology between the governments of closed and closing societies around the world. This exchange has led to more restrictive political and legal environments and an overall growing sophistication of threats leveraged against civil society. Collective action by the citizenry is being met by collective action between these oppressive states. In these closed and closing spaces civil society needs actionable intelligence that will allow them to rapidly identify new threats and respond to their changing threat landscape.
Activists and human rights defenders already spend a great deal of time working to identify, assess, monitor, and respond to the threats that they face. But, much of this information is trapped in a opaque collection of websites, news-feeds, reports, mailing lists, and wikis that are rarely shared widely enough to ensure that they can be found when needed. A change is needed that will allows activists and human rights defenders to not only to more quickly identify information important to them, but also to be able to source and share mitigations and strategies to respond to these threats. An actionable type of human rights intelligence is needed.
Luckily, the frameworks for these types of systems already exist in the cybersecurity threat & intelligence sharing field. This field fosters the sharing of structured intelligence about how to identify cyber threats they face - such as malware, DDOS attacks, and spam e-mails- and ways to mitigate those threats. This field is able to integrate outside threat intelligence into their work in near real time by automating the information exchange process using data that is atomized to a level where each component of data (such as URL’s, IP address’, and malware file) can easily be identified and used to train various security tools to respond to these current threats.
The cyber threat intelligence field is moving to a series of information sharing schemas so that analysts can provide a deeper understanding of each threat and their relationships with other threats in a machine readable format. The use of shared schemas provides a range of other benefits besides automation. By using shared schemas analysts are able to have a common understanding of the threats that they face. The schemas were also built with trust and privacy in mind. This allows groups to establish information sharing practices that put technical controls in place to prevent the disclosure of fields that might contain sensitive information or those that could run afoul of legal restrictions based upon the organization’s duty-of-care or the identity of the recipient they are sharing with.
Because the cyber-security community has a range of foci there are more than a few different schemas in use. For instance, one can share intelligence about cyber threats using the “Structured Threat Information eXpression” (STIX™). STIX uses definitions of “attack patterns” from the “Common Attack Pattern Enumeration and Classification” (CAPEC), the “Cyber Observable eXpression” (CybOX™) to share what was observed in an investigation, the “Common Vulnerabilities and Exposures” (CVE®), and/or “Common Vulnerability Reporting Framework” (CVRF) to describe the vulnerabilities that the threat leveraged to carry out their attack, and “Trusted Automated eXchange of Indicator Information” (TAXII™) for automating the exchange of the intelligence to be shared. This is just one slice of the wide array of data exchange specifications that make up the cyber-threat intelligence sharing landscape.
The cyber threat intelligence landscape organically built schemas within existing communities of practice and has been integrating those schemas to allow for wide scale threat intelligence sharing between these communities. Just like with the cyber security world Incorporating threat intelligence into the human rights community does not require that every human rights project adopt a single shared schema. If the human rights community focus on leveraging the lessons learned in the growth of the cyber threat intelligence community instead of where it is headed there are many lessons we can adopt to make human rights information able to be used by civil society worldwide to actively respond to the threats they face.
We can gain many of the tactical benefits of threat intelligence by making small changes in the way we collect, structure, share the information we collect for our projects. One easy first step for human rights organizations who are tracking data about human rights conditions is to seek out collaboration within small groups of related projects on how they can structure and share data strategically. By using shared, or overlapping, schemas for raw data we can create linkages between projects that provide deeper insight into the systemic nature of human rights issues.
One opportunity I see regularly is how properly structured collaboration and data could deepen the work of policy advocates and human rights abuse monitors. By actively looking for how to structure and share their data to support each other those conducting legislative transparency and legal analysis and those tracking unjust arrests based on those very same laws could gain a way to show the human impact of these laws and provide deep insight into how the laws are being misused. By building collaboration into the data itself civil society are able to more clearly provide narratives that show how laws are misused when advocating for reform.
I see an great opportunity for informing and supporting collective action through human rights threat intelligence. My goal is to find practical ways of supporting strategic threat intelligence in the human rights community. I invite any groups collecting human rights threat information to join me in working towards more rapid, collaborative, and actionable intelligence about human rights threats worldwide.
I will continue to document the lessons and best practices of human rights threat intelligence here on my website. In future articles I will write more about the different types of human rights threat intelligence; how to leverage elements of threat intelligence to build more impactful projects; how to build on existing formats for intelligence collection and exchange across human rights, law, and cyber-threat intelligence; mechanisms for supporting threat intelligence exchange; and models for threat intelligence exchange to support different purposes.